Phishing Email Assessment
Phishing Email Assessment
Protection Against Business Email Compromise (BEC)
Business Email Compromise (BEC) is a social engineered email scam that aims at extracting confidential business information or money through fraudulent requests for payment or wire transfer. Impersonation of a company’s CEO, senior executives, business partners or known contact of the victim, using a spoofed email account to send the request, is the most common method used by BEC attackers.
Email Security Gateways such as SpamZetta can remove unwanted spam emails that exhibit certain patterns or are sent from known blacklist sources. Unfortunately, BEC is social engineered carefully by attackers to slip through such algorithm based email security gateway. BEC related emails are highly targeted and specific to the victim’s day-to-day business dealings and could sometimes be sent from authentic mailboxes that have been used to communicate with the victim on daily basis.
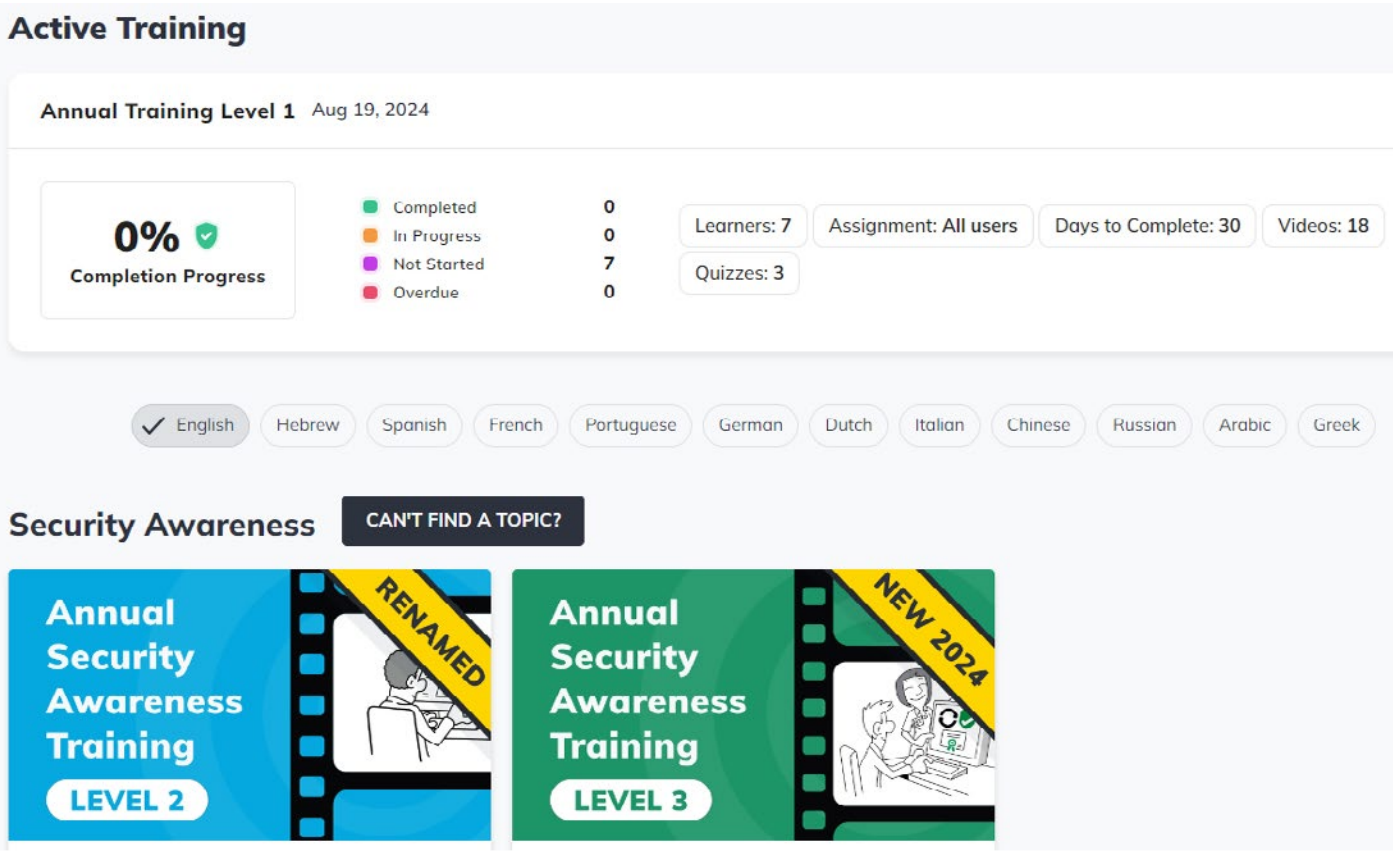
To combat BEC, vigilance among staff is important. This is where SecureAX Phishing Email Assessment helps minimise BEC risk within your organisation! This service covers three broad scopes :- Identifying & Targeting A Scenario, Conducting Phishing Simulation Email, and Providing Awareness Training to improve cybersecurity awareness within your company.
Protection Against Business Email Compromise (BEC)
Phishing Email Assessment
• Training on security awareness
• Phishing and ransomware
• Social engineering and password safety
• Multifactor authentication
• Device and data management
• Data privacy and compliance (e.g., GDPR)
• Social media and mobile safety
• Safe AI usage
• Domain-specific courses (e.g., ethics, financial services, remote work)
Contact us for a quote.
- Real-world phishing simulations
- Short 3-5 mins, interactive microlearning modules
- Automated training campaigns based on user roles and risk levels
- Comprehensive reporting & compliance tracking for GDPR, HIPAA, ISO 27001 etc
- Multilingual content supported